TripleNet: Image Generation for Joint Information Hiding and Asymmetric Encryption
Abstract
We propose a unified framework, TripleNet, to perform joint information hiding and asymmetric encryption, via an interplay of three different neural networks. Using two sets of images, from two distinct domains, we generate pairs of public keys and private keys using a convolutional network jointly trained for image reconstruction. Two conditional generative adversarial networks are used for public key based encryption and private key based decryption, respectively. We achieve public key-based encryption and private key-based decryption with a Triplet Cycle of Adversarial networks. We show that such interaction of the triplet can result in effective joint information hiding and encryption with neural networks, which has never been explored before as far as we are aware. The proposed framework is different from current cryptography and steganography schemes while integrating the advantages o both two kinds of methods. TripleNet provides robust security and the diversity of both keys. We conducted a comprehensive analysis to verify the effectiveness of TripleNet with various datasets, and provide a comparison with related image-to-image translation approaches for symmetric encryption and image steganography methods. Besides, our TripleNet can also be applied to encrypt multimedia data such as text and audio. Extensive experiments confirm TripleNet's effectiveness and security under various settings, in comparison with other most related approaches.
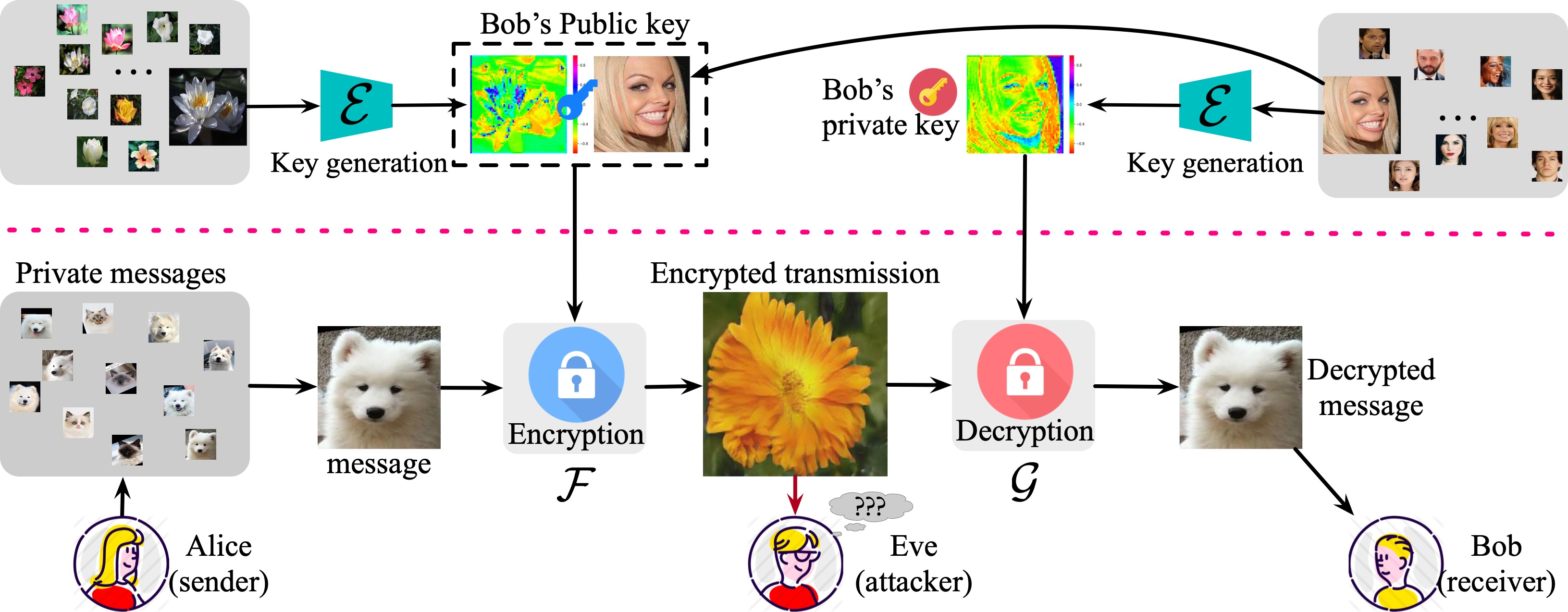
Architecture
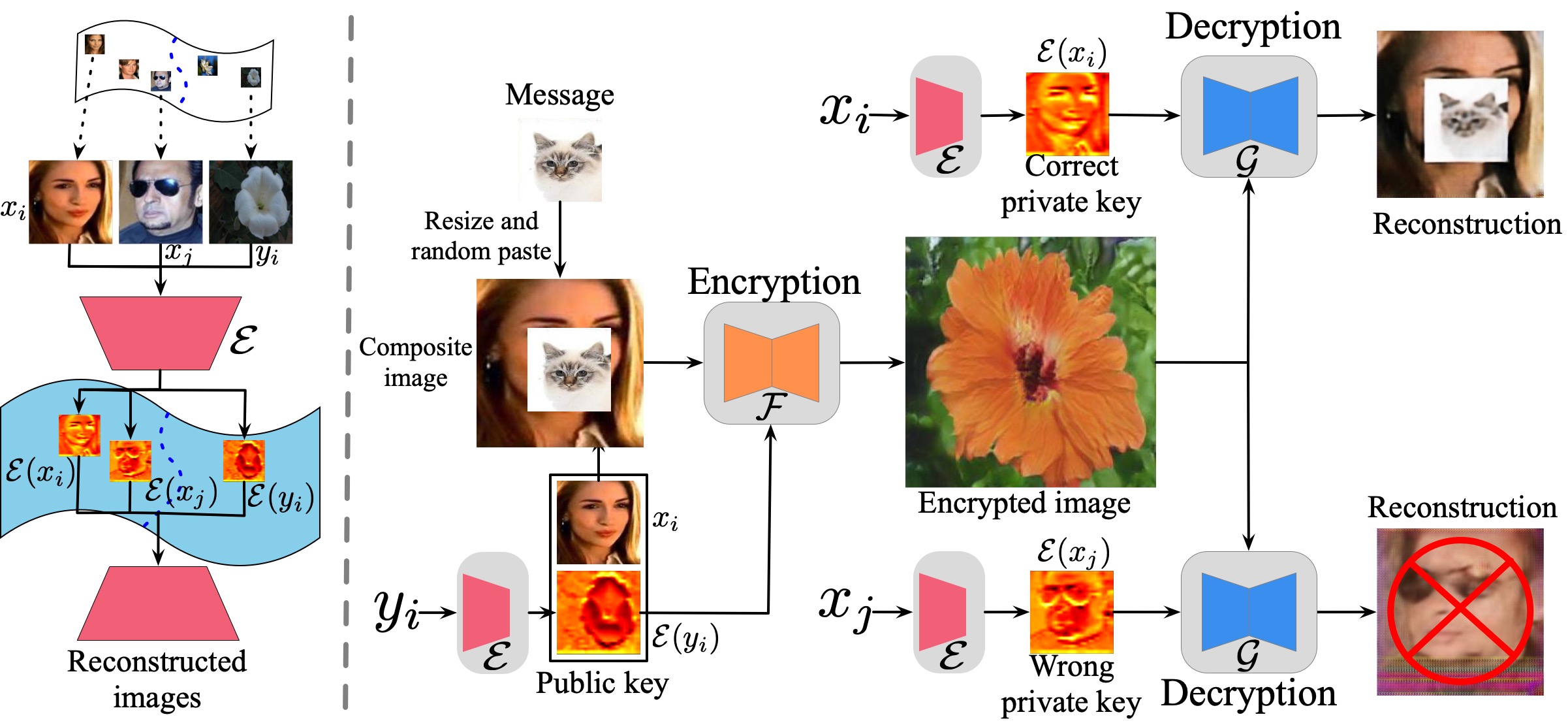
Comparison with previous work
Compared with previous symmetric encryption framework and steganography, we argue the proposed method have two main superiorities.
- Compared with cryptography algorithms, the encrypted output generated by our TripleNet looks like a natural image, which is misleading. Through this, our TripleNet can perform safe transmission without attracting other's attention.
- Even though the original cover is accessible or exposed by the public, the attacker cannot detect or decode the private message by comparing the original cover and the encrypted output. In other words, our method posses high security and robustness against statistical attacks.

Visual results
Visual encryption results at different settings. Left: the images in red box show the encryption and decryption results with varying values of α for interpolated images. Observe that the encrypted images are changed by adopting different α. Right: images in green box show the results of resizing and random pasting setting. Observe that the pasting location of the message image has a large impact on the synthesized images, which lead to diversified outputs. We show that the wrong private keys prevent the correct reconstruction of the private message.

Demo presentations
Encrypt the text into one image (asymmetric encryption)
We aim to encrypt private text information to an irrelevant image and perform the asymmetric encryption, which means that a wrong private key cannot lead to a successful reconstruction.
Encrypt the audio into one image (asymmetric encryption)
We aim to encrypt private an audio piece to an irrelevant image and perform the asymmetric encryption, which means that a wrong private key cannot lead to a successful reconstruction. Undesired noise! Attention!
Asymmetric image encryption (interpolation case)
We combine a private secret message image and an irrelevant container image to a composite image through a traditional image blending method. The we perform the asymmetric encryption. Varying values of α could lead to different encrypted outputs. A wrong private key cannot result in a correct reconstruction (only meaningless noise).
Asymmetric image encryption (smaller images (random paster))
To enhance the diversity of the encrypted outputs and promote the security of proposed TripleNet, we target to put a smaller size image to a larger container image. Thus, we could have a lot of different spatial choices. Changing the location could synthesize different synthesized outputs, which indicates a large sample diversity. A wrong private key cannot result in a correct reconstruction (only container image).
Analysis of sensitiveness of private key
We add different scales of Gaussian noise to the private key to evaluate the sensitiveness of the private key. More details could be found in our paper.
Citation
@article{zheng2019encryptgan,
title={EncryptGAN: Image Steganography with Domain Transform},
author={Zheng, Ziqiang and Liu, Hongzhi and Yu, Zhibin and Zheng, Haiyong and Wu, Yang and Yang, Yang and Shi, Jianbo},
journal={arXiv preprint arXiv:1905.11582},
year={2019}
}